Calendly Security
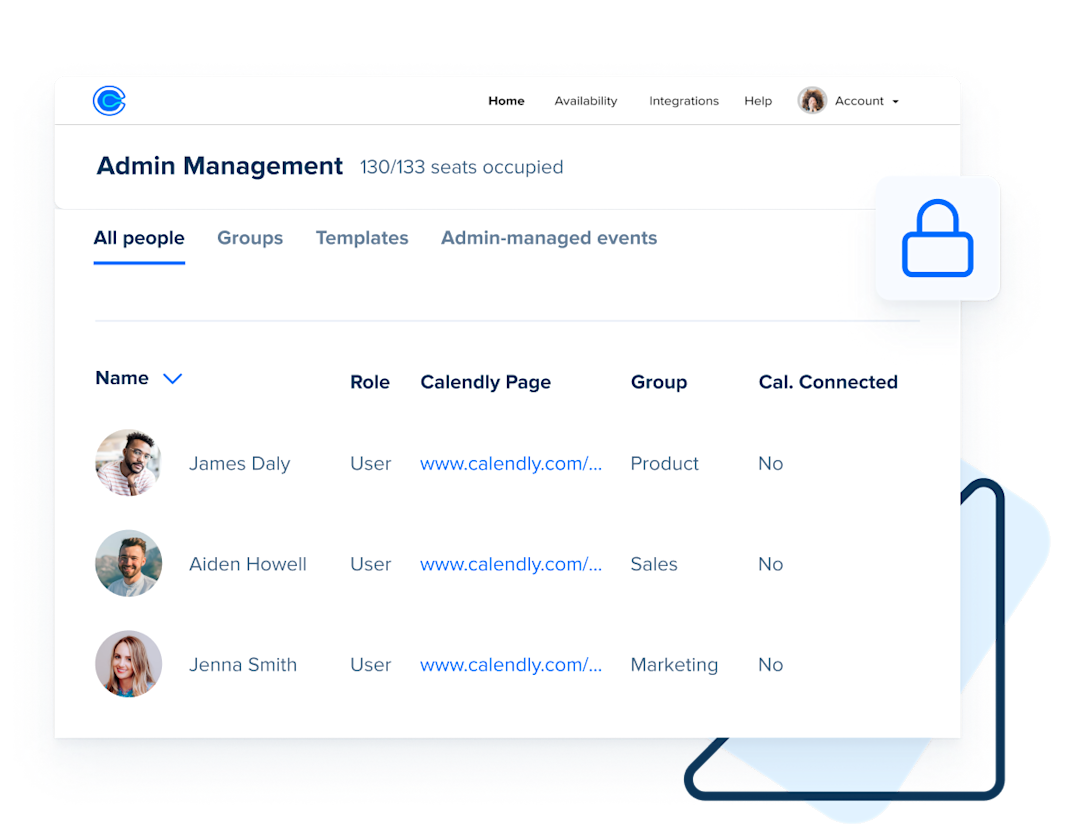
Calendly Security - Empower your remote workforce to schedule efficiently as a team. Calendly offers sso, scim, domain control, an activity log, and more. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check.
Calendly offers sso, scim, domain control, an activity log, and more. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Empower your remote workforce to schedule efficiently as a team.
Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Empower your remote workforce to schedule efficiently as a team. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Calendly offers sso, scim, domain control, an activity log, and more.
Security Calendly
Calendly offers sso, scim, domain control, an activity log, and more. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to.
Calendly vs Which is the best scheduling platform?
Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Empower your remote workforce to schedule efficiently as a team. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering.
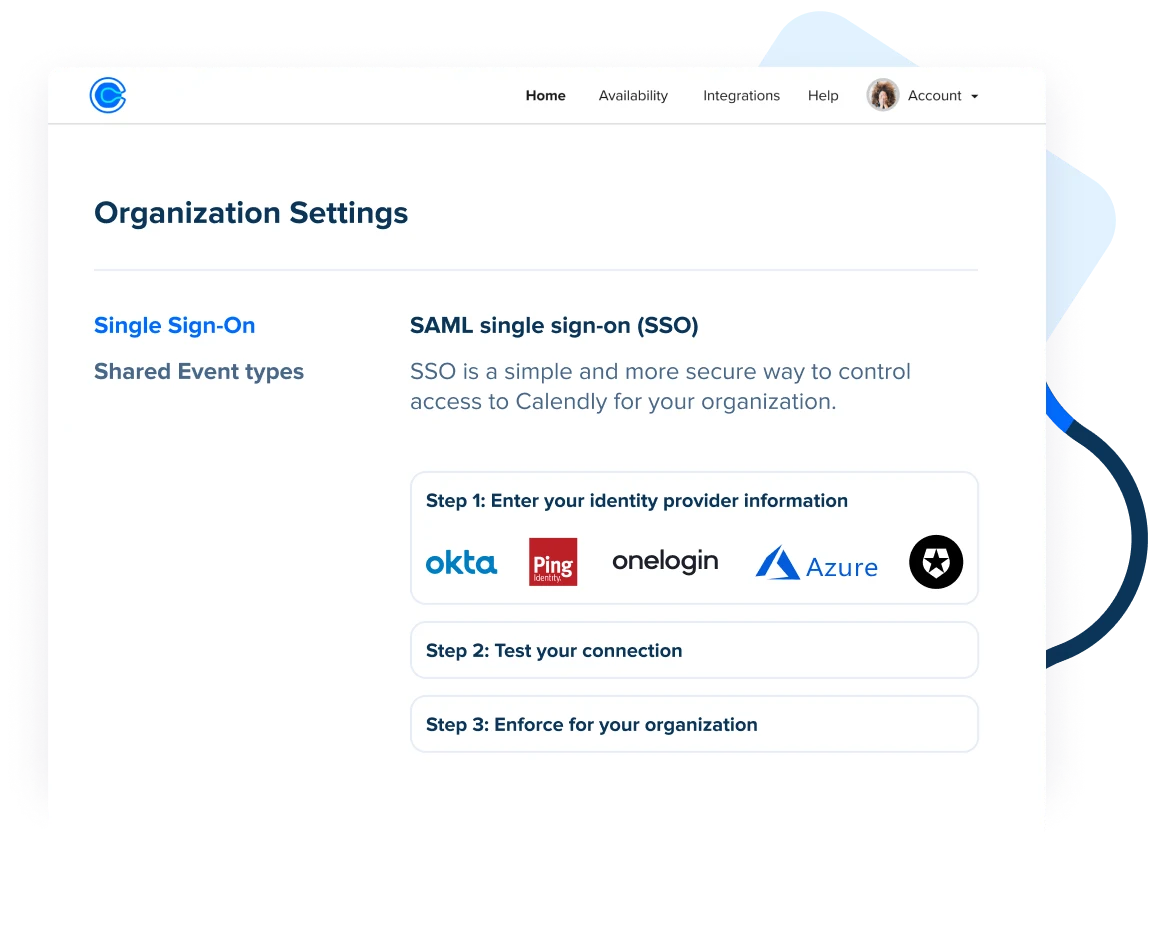
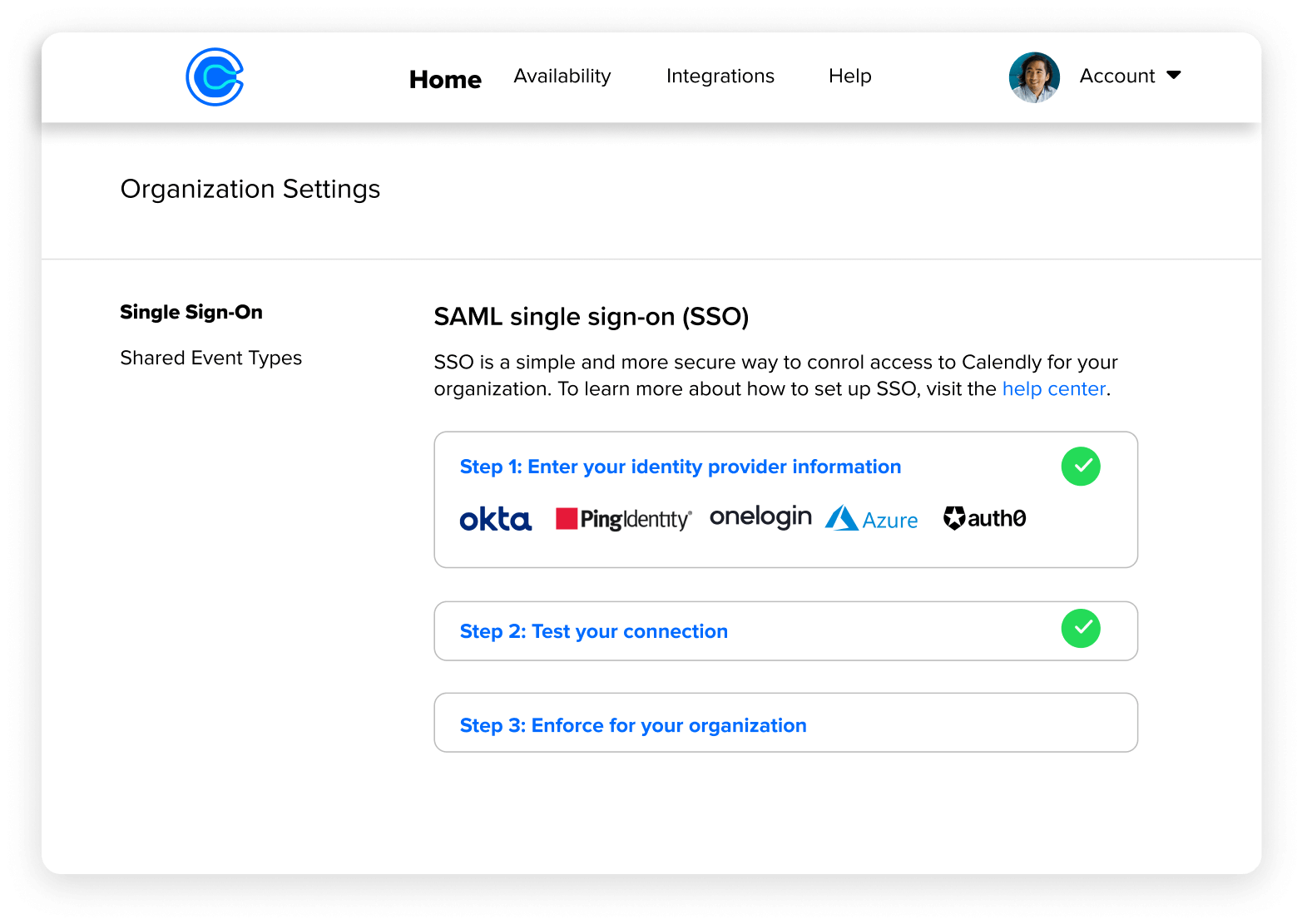
Calendly Single Sign On (SSO) SAML OAuth LDAP MFA
Calendly offers sso, scim, domain control, an activity log, and more. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Empower your remote workforce to schedule efficiently as a team. Phishing actors are actively abusing calendly.
캘린들리 리뷰, 가격, 기능, 장단점
Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Empower your remote workforce to schedule efficiently as a team. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering.
Security Calendly
Empower your remote workforce to schedule efficiently as a team. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Calendly offers sso, scim, domain control, an activity log, and more. Read about.
Security Calendly
Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Empower your remote workforce to schedule efficiently as a team. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering.
Security Calendly
Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Empower your remote workforce to schedule efficiently.
Information Technology Scheduling Software Calendly
Empower your remote workforce to schedule efficiently as a team. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Calendly offers sso, scim, domain control, an activity log, and more. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Phishing actors are actively abusing calendly.
Calendly vs Chili Piper Which One Is Better?
Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Empower your remote workforce to schedule efficiently as a team. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Read about how we handle cookies, uphold your data rights and ensure you.
Information Technology Scheduling Software Calendly
Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Empower your remote workforce to schedule efficiently as a team. Calendly offers sso, scim, domain control, an activity log, and more. Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Phishing actors are actively abusing calendly.
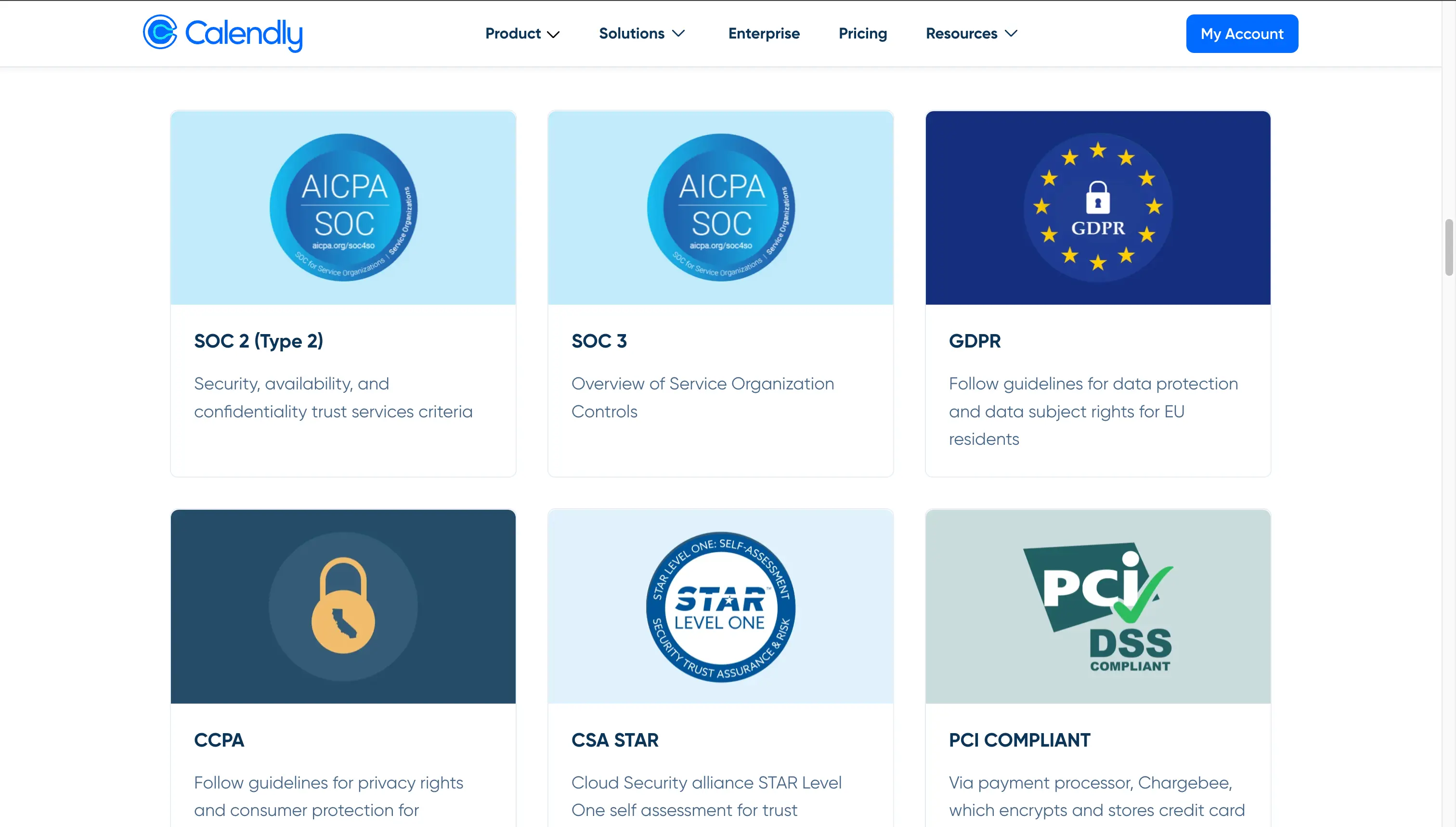
Read About How We Handle Cookies, Uphold Your Data Rights And Ensure You Remain Gdpr Compliant.
Empower your remote workforce to schedule efficiently as a team. Calendly is a cloud service that simplifies meeting scheduling by securely connecting to calendar providers to check. Phishing actors are actively abusing calendly to kick off a clever sequence to trick targets into entering their email account. Calendly offers sso, scim, domain control, an activity log, and more.